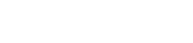The technological strides that have been made over the past ten years have resulted in dramatic changes in the way we view safety and security. While it used to be enough to lock your doors, install a safe for your important documents, and own a safety deposit box, in this day and age, everything a person needs to steal your identity is with you at all times. Cell phones and computers have become hackers’ best friends.
Accordingly, data breaches have become established companies’ worst nightmare. When customer information is compromised through their systems, it’s an embarrassment that deeply affects their credibility. Beyond that, hackers who get around security protocols and access systems are free to steal hundreds of thousands of data files. As the realms of physical and cybersecurity merge, Kastle continues to innovate to keep our clients and their access data protected. Having a cloud-based platform with clients’ data stored separately from their on-site network is an example. To get a sense of the extent that data violations have become more frequent we compiled a list of major data breaches to date from 2004-2019. Our findings are below.
Over the past 15 years, the top 5 types of records that hackers have collected are financial, web, social networks, hotel, and retail which together account for over 4.3 billion records.. Meanwhile, fewer than 20,000 records were political in nature.
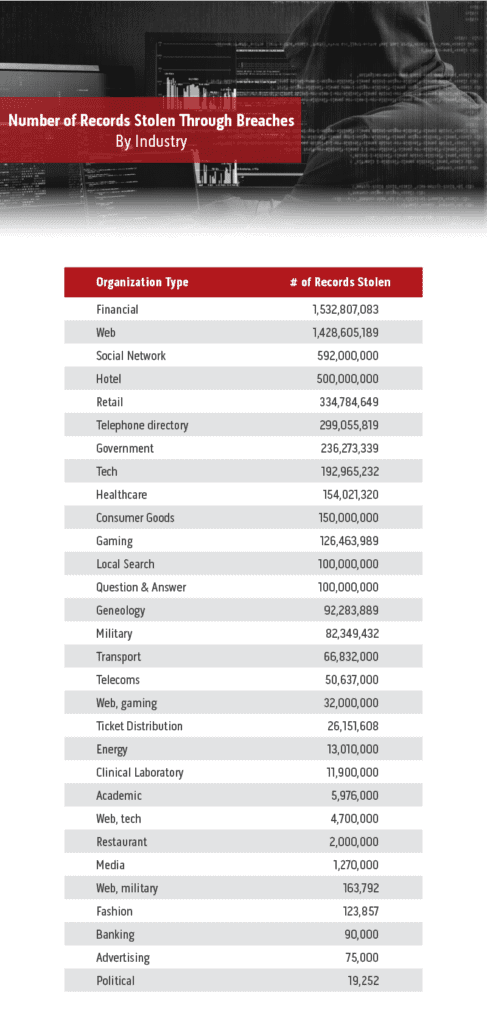
Based on the number of records stolen, First American Corporation has had the most serious data breach to date with 885 million records impacted. Facebook also had a well-publicized breach that left just under 600 million records accessed, followed by Marriot with 500 million. A few major retailers also made the top 25 list, including Under Armor, Target Corporation, TJ Maxx, and Sony Playstation.
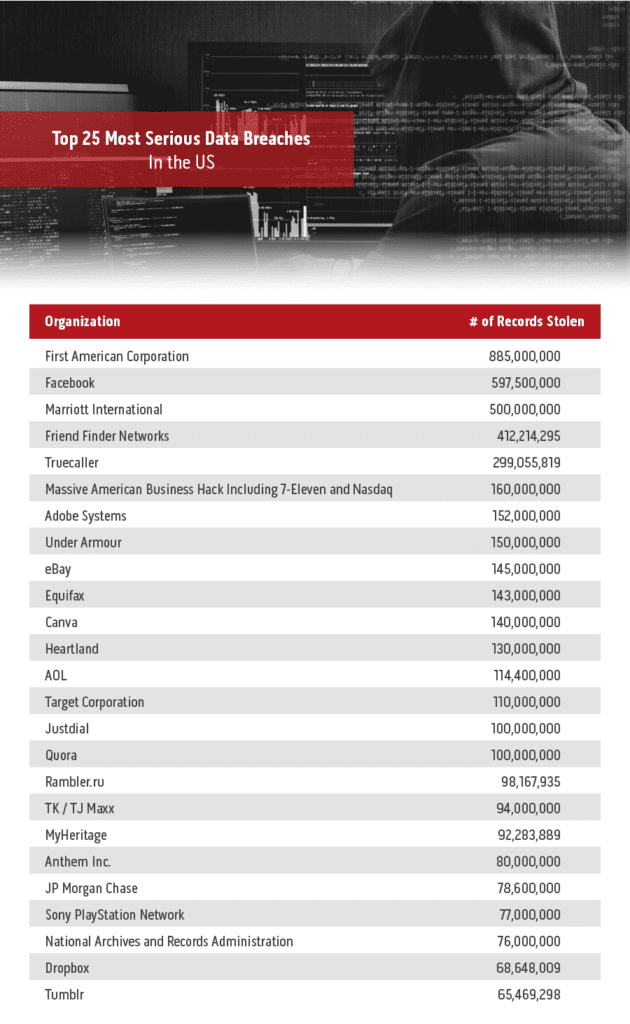
There are several ways that data breaches can occur through either hacking or poor security. Malware is a very popular tool used to compromise victims’ computers, in fact in Q2 of 2018, nearly 50% of data breaches were through malware. There are various methods of introducing malware to people’s computers, mostly through compromising servers or workstations.
Social engineering was used in around a quarter of Q2 2018 data breaches, meaning cybercriminals manipulated users into thinking that a message or attachment is from a trusted source and then infect the operating system with malware when the message has been opened. And of course, hacking plays a role in almost all data breaches as the first step in an attack. By gaining access to vulnerabilities in the system, cybercriminals can exploit weaknesses in security and tailor their strategy according to the openings they find.
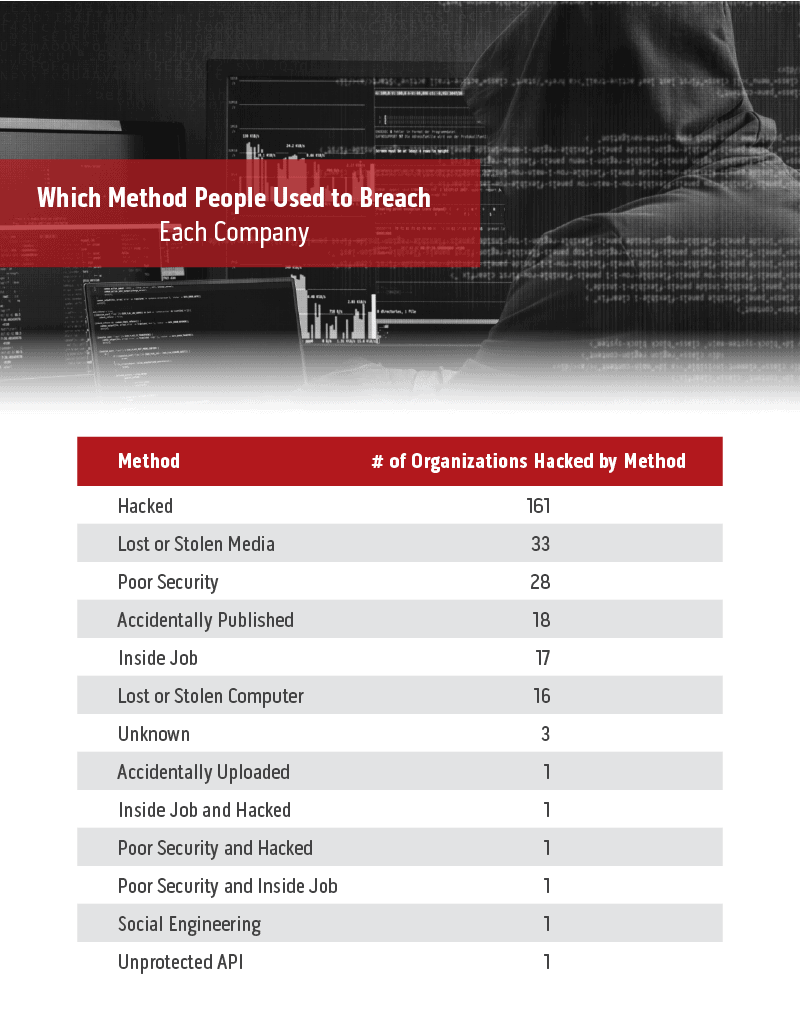
In the majority of cases in the past decade, hacking was the method used to compromise security. The next steps may have varied, but the initial breach was due to a cybercriminal hacking into the system to exploit vulnerabilities. However, there are plenty of other methods that people can use to access protected information from lost or stolen media, accidentally published information, or poor security in general. In fact, 30 of the breaches were related in some way to poor security. This casts a troubling light over the overall security of companies entrusted with client information. It’s a risky business, to hold information that outsiders would like access to without making sure that security is as strong as possible.
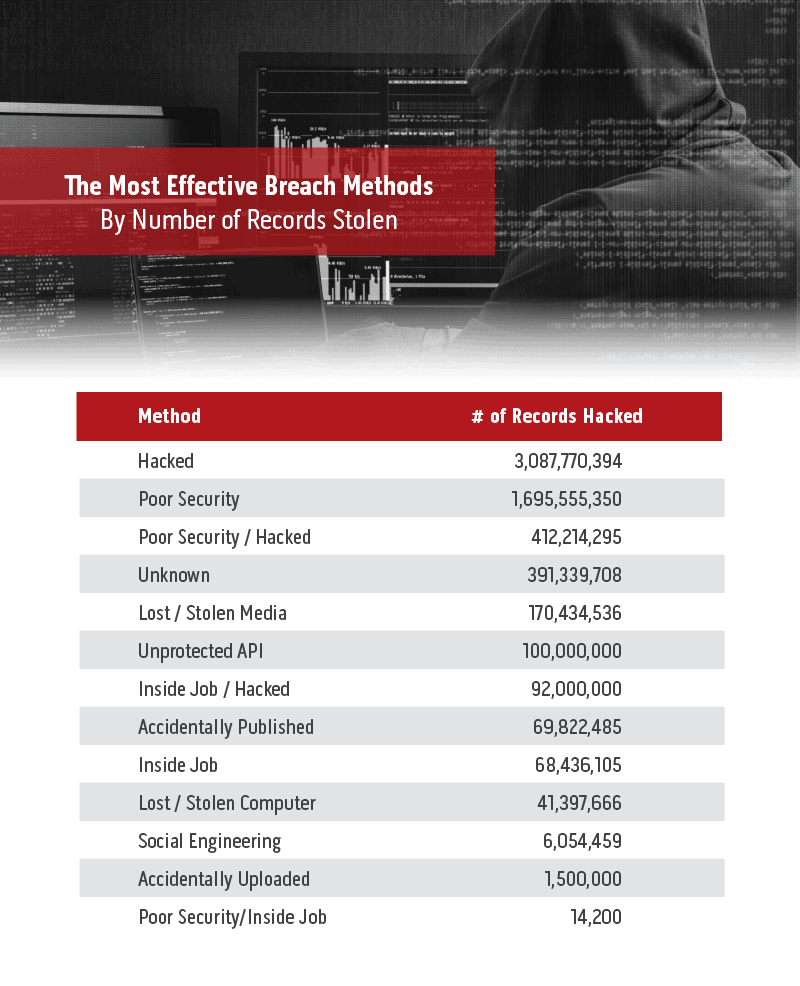
Data breaches that began with a hack of some kind resulted in over 3 billion private records being stolen. As stated above, nearly 50% of data breaches are achieved through the use of malware. In 2018, email spam was the most common way cybercriminals were able to spread malware to company systems. In 69% of cases, spam emails are designed to trick users into using a URL that will allow them to introduce malware to the system. Overall, 32% of data breaches in 2018 used phishing attacks were the method used to access the system.
Of course, in some cases, hacking isn’t the opening used by cybercriminals to steal records. The second and third most effective data breach methods were either straightforward poor security or poor security that allowed a person to hack the system. Additionally, human error is a factor in security. Accidentally published and uploaded records and documents can cause problems, as can lost or stolen media or computers.
Cybercriminals can even infiltrate your network through your security system, such as through IP video surveillance cameras. For instance, many businesses fail to change the default manufacturer passwords that come with their cameras at purchase and hackers use those "universal" passwords to enter the network via the camera's internet connection. That's why a cloud-based security system (like Kastle) is more secure -- the security components communicate directly to the secure offsite server and never intermingle with the on-site network.
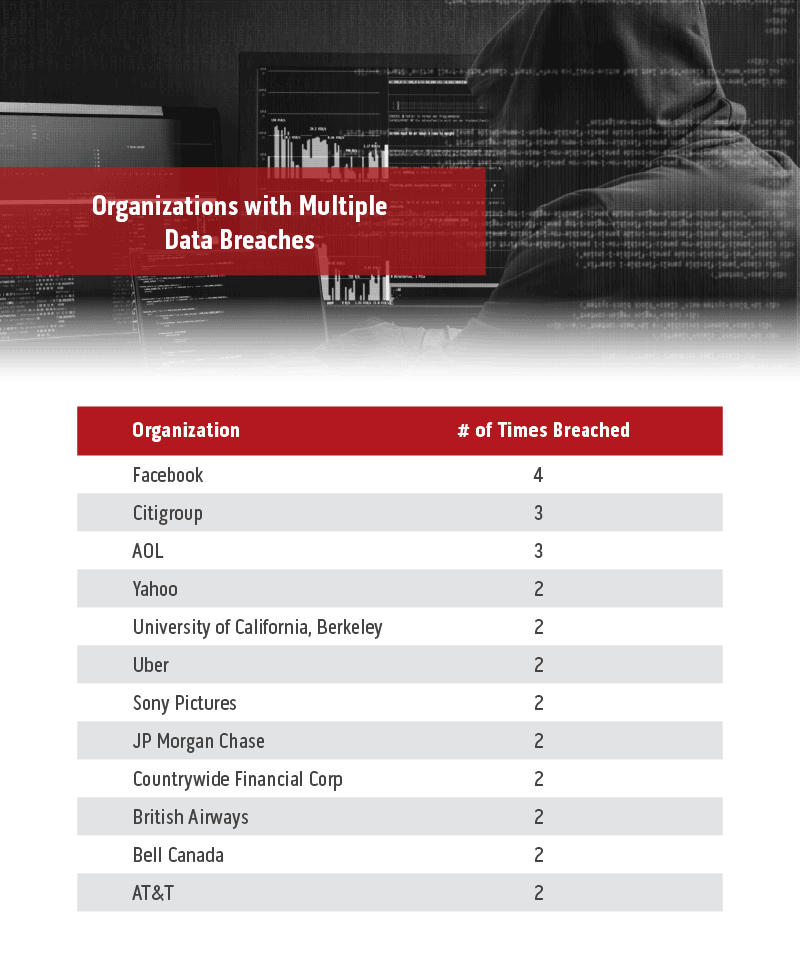
Facebook has been the most frequent victim of hacks over the past 15 years, with 4 data breaches, followed by Citigroup and AOL, each with 3 breaches. Overall, there have been 12 companies that have had multiple breaches since 2004.
Data breaches are an ongoing problem in today's business world. As recently as May 4, 2019, DoorDash experienced a massive hack that compromised 4.9 million customer’s data. Amongst this data were their names, email addresses, delivery addresses, phone numbers, order history, and partial passwords. The last 4 digits of customer credit cards were revealed as well. On the employee side, driver’s license numbers for over 100,000 delivery personnel were exposed. The actual incident was only discovered in September, but the actual breach occurred in early May. This has lead to a commentary on how vulnerable customer information is when given to businesses who don’t take proper security measures, both with their physical business and their online data.
While shoring up your online security is critical to preventing data breaches, physical access is another vulnerability that hackers can exploit. Our team specializes in Physical Access Control (PAC) systems, ensuring that your PAC will never be the point of entry hackers exploit to use your data. This includes preventing hacks through your IP video cameras as well as protecting your access control server against malware. We remove those connections to your on-site network by placing them in a cloud-based access control platform, keeping your information safe and secure. If you’re looking for a Physical Access Control System for your company, contact us here. Our team would love to help!